Mastering Cybersecurity with the MITRE ATT&CK Framework
The MITRE ATT&CK framework is a valuable tool for organizations seeking to enhance their cybersecurity posture. By providing a comprehensive knowledge base of tactics and techniques employed by cyber attackers, the framework allows organizations to develop more effective incident response plans and threat intelligence strategies. Through this approach, organizations can gain a better understanding of the threat landscape, including the specific threats they face and how to defend against them.
One of the key features of the MITRE ATT&CK framework is its interactive visualization tool, the MITRE ATT&CK Matrix. This tool allows users to explore the tactics, techniques, and procedures used by attackers in detail. By using the Matrix, organizations can identify gaps in their security posture and develop more effective security measures. Compared to older frameworks like the Cyber Kill Chain and the Diamond model, which only focus on specific stages of an attack, the MITRE ATT&CK framework indexes all aspects of an attack from both the attacker and the defender’s perspective. With its widespread adoption, the MITRE ATT&CK framework has become the most widely adopted cybersecurity framework used today, providing a powerful tool for organizations to better understand and defend against cyber threats.
Understanding MITRE ATT&CK Tactics and Techniques
The MITRE ATT&CK framework is a comprehensive tool for understanding the tactics and techniques used by cyber adversaries. It breaks down the attack lifecycle into 14 tactics that are categorized based on the objectives of the attackers. These tactics include Reconnaissance, Resource development, Initial access, Execution, Persistence, Privilege escalation, Defense evasion, Credential access, Discovery, Lateral movement, Collection, Command and Control, Exfiltration, and Impact.
Each of these tactics encompasses a range of techniques that adversaries use to achieve their goals. For instance, techniques under the Execution tactic include code signing, DLL side-loading, and PowerShell, while techniques under the Persistence tactic include Registry Run Keys and Services. Adversaries may use different techniques depending on factors such as their skill sets, the configuration of the system they are attacking, and the availability of necessary tools.
The MITRE ATT&CK framework includes a total of 193 techniques and 401 sub-techniques identified for enterprises. For each technique, the framework provides detailed information, such as a description of how it works, the systems it pertains to, which known attacker groups use it, ways to mitigate its impact, and references to its use in the wild. By understanding the tactics and techniques used by adversaries, organizations can better assess their risk and develop more effective defenses. The MITRE ATT&CK Matrix is an invaluable tool for identifying gaps in an organization's security posture and developing a more robust security strategy.
Common Attack Techniques and Mitigation Strategies
One of the key benefits of using the MITRE ATT&CK framework is the ability to identify common attack techniques and develop strategies to mitigate them. By understanding how attackers operate, organizations can implement more effective defenses and reduce the risk of successful attacks.
For example, the Execution tactic includes techniques such as code signing, DLL side-loading, and PowerShell. To mitigate these techniques, organizations can use techniques such as code signing policies, whitelisting, and limiting access to PowerShell. Similarly, the Persistence tactic includes techniques such as Registry Run Keys and Services, which can be mitigated through methods such as removing unnecessary accounts and limiting the use of domain accounts.
MITRE ATT&CK Matrix
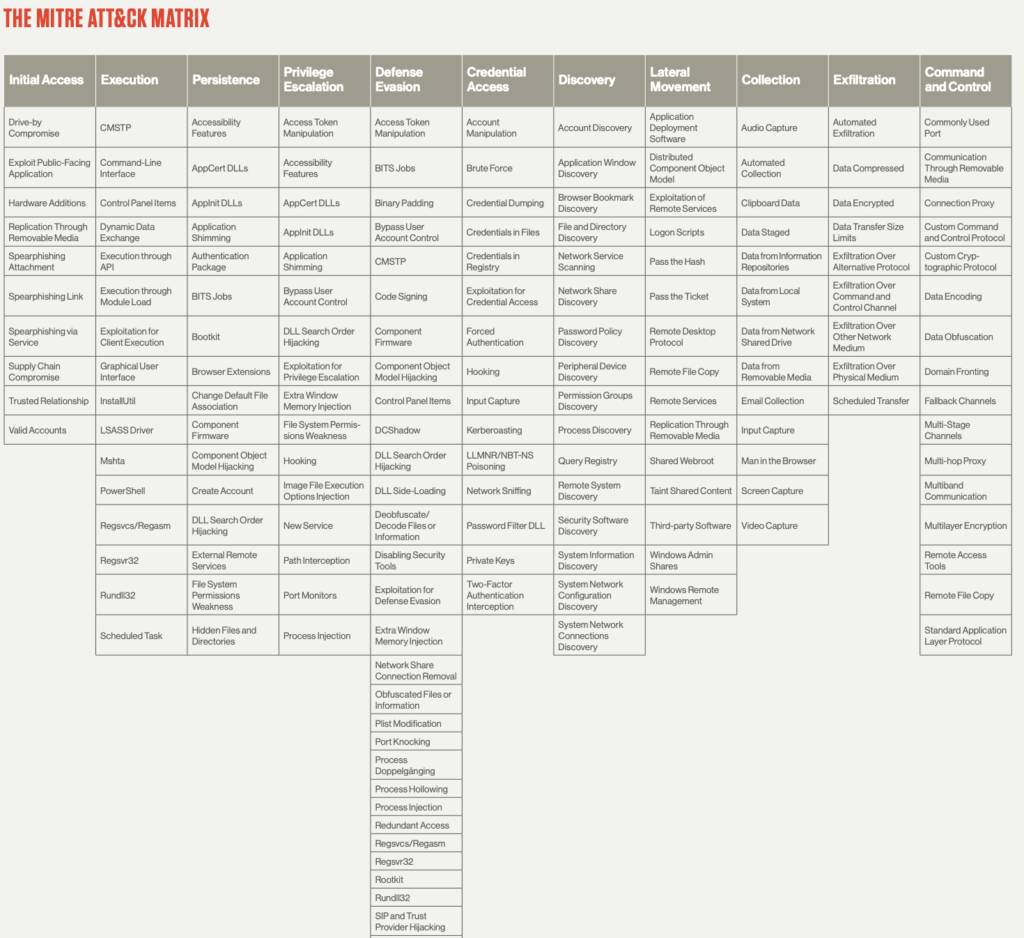
MITRE ATT&CK Matrix Use Cases:
The MITRE ATT&CK Matrix is a valuable tool for organizations to assess and improve their cybersecurity posture. Here are some ways in which the matrix can be used:
-
Perform a comprehensive security gap analysis and data security plan improvements: Using the MITRE ATT&CK framework, organizations can evaluate their current security measures and identify areas that need improvement. By mapping their security controls against the tactics and techniques used by real-world adversaries, organizations can develop a more comprehensive and effective security plan.
-
Strengthen cyber threat intelligence: The MITRE ATT&CK Matrix provides a wealth of information about the tactics and techniques used by adversaries. By using this information, organizations can develop more accurate and actionable threat intelligence. This intelligence can then be used to identify potential threats and vulnerabilities, enabling organizations to take proactive measures to prevent attacks.
-
Enhance Alert Triaging and Investigation: The MITRE ATT&CK Matrix can be used to prioritize alerts and focus on the most critical threats. By mapping alerts to the relevant tactics and techniques in the matrix, security teams can quickly identify the nature of the attack and take appropriate action. This also helps in reducing alert fatigue and improving the efficiency of the security team.
-
Create realistic scenarios for team exercises and attack emulations: The MITRE ATT&CK Matrix can be used to develop realistic scenarios for team exercises and attack simulations. These exercises can help organizations prepare for real-world attacks and identify areas that need improvement. By using the matrix to develop scenarios, organizations can ensure that their exercises are relevant and effective.
-
Assess security maturity of the Security Operations Center (SOC): The MITRE ATT&CK Matrix can be used to evaluate the effectiveness of the security operations center (SOC) and identify areas that need improvement. By mapping the security controls and processes used by the SOC against the tactics and techniques in the matrix, organizations can assess their security maturity and identify areas that need improvement.
-
Communicate effectively and efficiently to stakeholders: The MITRE ATT&CK Matrix provides a common language for communicating about cybersecurity threats and risks. By using the matrix to describe potential threats and vulnerabilities, organizations can communicate effectively and efficiently with stakeholders such as executives, board members, and external partners.
-
Establish a common language for working with vendors and consultants: The MITRE ATT&CK Matrix can be used to establish a common language for working with vendors and consultants. By using the matrix to describe the organization's security requirements and the tactics and techniques used by adversaries, organizations can ensure that their vendors and consultants understand their needs and can provide appropriate solutions.
Applying the MITRE ATT&CK Framework to Threat Intelligence
The MITRE ATT&CK framework can also be used in conjunction with threat intelligence to better understand and respond to threats. Threat intelligence provides information on known or potential attacks, including the tactics and techniques used by adversaries.
By mapping threat intelligence data to the MITRE ATT&CK framework, organizations can identify which tactics and techniques are being used by specific threat actors and develop more targeted and effective defenses. This can also help organizations to identify gaps in their security posture and prioritize security investments.
Best Practices for Using the MITRE ATT&CK Framework
The MITRE ATT&CK Framework can be an extremely powerful tool for enhancing an organization's cybersecurity posture, but it's important to use it correctly. Here are some best practices for using the framework effectively:
- Identify your organization's most valuable assets: Before using the MITRE ATT&CK Framework, it's important to identify which of your organization's assets are most valuable and what kind of attacks they're most vulnerable to. This will help you prioritize your use of the framework and develop more effective defenses.
- Involve all relevant stakeholders: The MITRE ATT&CK Framework can be useful for a wide range of stakeholders, including security analysts, incident response teams, and C-level executives. It's important to involve all relevant stakeholders in the process of using the framework to ensure that everyone is on the same page and working towards the same goals.
- Continuously update your understanding of threats: The threat landscape is constantly changing, and new threats are emerging all the time. It's important to continuously update your understanding of threats and ensure that you're incorporating the latest information into your use of the MITRE ATT&CK Framework.
- Use the framework in conjunction with other tools: The MITRE ATT&CK Framework is just one tool in your cybersecurity toolbox. To develop a robust and effective cybersecurity strategy, it's important to use the framework in conjunction with other tools, such as vulnerability scanners and security information and event management (SIEM) systems.
Limitations of the MITRE ATT&CK Framework
While the MITRE ATT&CK Framework is a valuable tool for enhancing an organization's cybersecurity posture, it's important to recognize its limitations. Here are some limitations of the framework:
- It's not a one-size-fits-all solution: The MITRE ATT&CK Framework is a general framework that can be applied to many different organizations, but it's not a one-size-fits-all solution. Different organizations have different security needs and vulnerabilities, and it's important to tailor the use of the framework to those specific needs.
- It's not a replacement for skilled personnel: The MITRE ATT&CK Framework is a tool that can help security analysts and incident response teams do their jobs more effectively, but it's not a replacement for skilled personnel. To use the framework effectively, you need skilled personnel who can analyze and interpret the information provided by the framework.
- It's not a guarantee of security: Using the MITRE ATT&CK Framework can help organizations identify gaps in their cybersecurity posture and develop more effective defenses, but it's not a guarantee of security. No tool or framework can completely eliminate the risk of a cyberattack, and organizations need to remain vigilant and proactive in their cybersecurity efforts=
The Future of the MITRE ATT&CK Framework
The MITRE ATT&CK framework is a constantly evolving tool that is updated regularly to reflect changes in the threat landscape. In the future, we can expect to see continued updates and enhancements to the framework, as well as new tools and technologies for using it.
For example, the MITRE ATT&CK team is currently working on a new tool called ATT&CK for Containers, which will provide a framework for assessing and mitigating security risks in container environments. We can also expect to see more emphasis on the use of the framework in areas such as threat hunting, incident response, and red teaming. As the threat landscape continues to evolve, the MITRE ATT&CK framework will remain a critical tool for organizations looking to stay ahead of the curve.
Mitigating Cybersecurity Risks with MITRE ATT&CK Framework
The MITRE ATT&CK framework is an invaluable tool for organizations to identify and mitigate cybersecurity risks. By categorizing tactics and techniques used by adversaries, businesses can better assess their risk and develop more effective defenses.
Using the framework, organizations can perform a security gap analysis, enhance cyber threat intelligence, and create realistic scenarios for team exercises and attack emulations. It can also be used to assess the security maturity of the Security Operations Center (SOC), communicate effectively to stakeholders, and establish a common language for working with vendors and consultants.
By implementing the MITRE ATT&CK framework, businesses can improve their cybersecurity posture and better protect against potential threats. It's important to note that the framework doesn't cover all aspects of cybersecurity. To gain a deeper understanding of network security, consider exploring the OSI model, which breaks down the different layers of network communication and can be useful in identifying vulnerabilities and implementing effective security measures. Together, the MITRE ATT&CK framework and the OSI model can help businesses build a stronger defense against cyber threats.






